应用安全性改进计划是向 Google Play 应用开发者提供的一项服务,用于提高其应用的安全性。该计划会提供关于构建更安全应用的提示和建议,并指出您的应用在上传到 Google Play 后需要采取增强措施的潜在安全漏洞。迄今为止,该计划已帮助开发者在 Google Play 上修复了超过 100 万款应用。
工作方式
在任何应用获准在 Google Play 上发布之前,我们都会对其进行安全扫描,包括扫描潜在的安全问题。我们还会持续不断地反复扫描 Google Play 上超过 100 万款的应用,以查找其他威胁。
如果您的应用被标记为存在潜在安全问题,我们会立即通知您,以帮助您快速解决该问题并确保用户安全。我们会使用电子邮件和 Google Play 管理中心向您发送提醒,并提供指向支持页面的链接,其中详细说明了如何改进应用。
通常,这些通知会包含尽快向用户提供改进的时间表。对于某些类型的问题,我们可能会要求您先改进应用的安全性,然后才能发布应用的更多更新。
您可以向 Google Play 管理中心上传新版本的应用,以确认您已完全解决了相应问题。请务必递增已修复应用的版本号。过几个小时后,请在 Play 管理中心检查安全提醒;如果提醒已不存在,就表示没有任何问题。
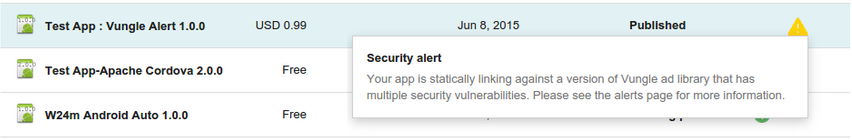
Play 管理中心内某个应用的安全性改进提醒示例。
参与其中
此计划的成功取决于我们与您(Google Play 上的应用开发者)以及安全社区的合作。我们都有责任为用户提供安全可靠的应用。如有任何反馈或疑问,请通过 Google Play 开发者帮助中心与我们联系。如需报告应用中的潜在安全问题,请通过 security+asi@android.com 与我们联系。
活动和修复
下面是 Google Play 应用开发者需注意的最新安全问题。点击各活动的支持页面链接即可查看漏洞和修复详情。
表 1:警告活动及相关的修复期限。
| 活动 | 已开始 | 支持页面 |
|---|---|---|
| 公开的 Firebase Cloud Messaging 服务器密钥 | 10/12/2021 | 支持页面 |
| Intent 重定向 | 5/16/2019 | 支持页面 |
| JavaScript 界面注入 | 12/4/2018 | 支持页面 |
| 配置盗用 | 11/15/2018 | 支持页面 |
| 跨应用脚本 | 10/30/2018 | 支持页面 |
| 文件级跨网站脚本 | 6/5/2018 | 支持页面 |
| SQL 注入 | 6/4/2018 | 支持页面 |
| 路径遍历 | 9/22/2017 | 支持页面 |
| 主机名验证不安全 | 11/29/2016 | 支持页面 |
| Fragment 注入 | 11/29/2016 | 支持页面 |
| Supersonic 广告 SDK | 9/28/2016 | 支持页面 |
| Libpng | 6/16/2016 | 支持页面 |
| Libjpeg-turbo | 6/16/2016 | 支持页面 |
| Vpon 广告 SDK | 6/16/2016 | 支持页面 |
| Airpush 广告 SDK | 3/31/2016 | 支持页面 |
| MoPub 广告 SDK | 3/31/2016 | 支持页面 |
| OpenSSL(“logjam”和 CVE-2015-3194、CVE-2014-0224) | 3/31/2016 | 支持页面 |
| TrustManager | 2/17/2016 | 支持页面 |
| AdMarvel | 2/8/2016 | 支持页面 |
| Libupup (CVE-2015-8540) | 2/8/2016 | 支持页面 |
| Apache Cordova (CVE-2015-5256、CVE-2015-1835) | 12/14/2015 | 支持页面 |
| Vitamio 广告 SDK | 12/14/2015 | 支持页面 |
| GnuTLS | 10/13/2015 | 支持页面 |
| Webview SSLErrorHandler | 7/17/2015 | 支持页面 |
| Vungle 广告 SDK | 6/29/2015 | 支持页面 |
| Apache Cordova(CVE-2014-3500、CVE-2014-3501 和 CVE-2014-3502) | 6/29/2015 | 支持页面 |
表 2:仅发出警告的活动(无修复期限)。
| 活动 | 已开始 | 支持页面 |
|---|---|---|
| 隐式 PendingIntent | 2/22/2022 | 支持页面 |
| 隐式内部 intent | 6/22/2021 | 支持页面 |
| 不安全的加密模式 | 10/13/2020 | 支持页面 |
| 不安全的加密模式 | 9/17/2019 | 支持页面 |
| Zipfile 路径遍历 | 5/21/2019 | 支持页面 |
| 嵌入式 Foursquare OAuth 令牌 | 9/28/2016 | 支持页面 |
| 嵌入式 Facebook OAuth 令牌 | 9/28/2016 | 支持页面 |
| Google Play 结算服务拦截 | 7/28/2016 | 支持页面 |
| 嵌入式 Google 刷新令牌 OAuth | 7/28/2016 | 支持页面 |
| 开发者网址泄露凭据 | 6/16/2016 | 支持页面 |
| 嵌入式密钥库文件 | 10/2/2014 | |
| Amazon Web Services 嵌入式凭据 | 6/12/2014 |
