Google से साइन इन करें सुविधा की मदद से, अपने Android ऐप्लिकेशन में उपयोगकर्ता की पुष्टि करने की सुविधा को आसानी से इंटिग्रेट किया जा सकता है. उपयोगकर्ता, अपने Google खाते का इस्तेमाल करके आपके ऐप्लिकेशन में साइन इन कर सकते हैं, सहमति दे सकते हैं, और अपनी प्रोफ़ाइल की जानकारी को आपके ऐप्लिकेशन के साथ सुरक्षित तरीके से शेयर कर सकते हैं. Android की Credential Manager Jetpack लाइब्रेरी, इस इंटिग्रेशन को आसान बनाती है. साथ ही, एक ही एपीआई का इस्तेमाल करके, Android डिवाइसों पर एक जैसा अनुभव देती है.
इस दस्तावेज़ में, Android ऐप्लिकेशन में 'Google से साइन इन करें' सुविधा को लागू करने का तरीका बताया गया है. साथ ही, इसमें 'Google से साइन इन करें' बटन का यूज़र इंटरफ़ेस (यूआई) सेट अप करने और ऐप्लिकेशन के हिसाब से ऑप्टिमाइज़ किए गए, एक टैप से साइन अप और साइन इन करने की सुविधा को कॉन्फ़िगर करने का तरीका बताया गया है. डिवाइस को आसानी से माइग्रेट करने के लिए, 'Google से साइन इन करें' सुविधा में अपने-आप साइन इन करने की सुविधा उपलब्ध है. साथ ही, यह सुविधा Android, iOS, और वेब प्लैटफ़ॉर्म पर काम करती है. इससे आपको किसी भी डिवाइस पर अपने ऐप्लिकेशन में साइन इन करने की सुविधा देने में मदद मिलती है. अगर आपने अपने ऐप्लिकेशन के लिए Firebase Authentication का इस्तेमाल किया है, तो Android पर Google से पुष्टि करें गाइड में, 'Google से साइन इन करें' और Credential Manager को इंटिग्रेट करने के बारे में ज़्यादा जानें.
'Google से साइन इन करें' सुविधा सेट अप करने के लिए, यह तरीका अपनाएं:
क्रेडेंशियल मैनेजर के बॉटम शीट यूज़र इंटरफ़ेस (यूआई) के लिए, 'Google से साइन इन करें' को एक विकल्प के तौर पर कॉन्फ़िगर करें. इसे इस तरह कॉन्फ़िगर किया जा सकता है कि उपयोगकर्ता को साइन इन करने के लिए अपने-आप प्रॉम्प्ट मिले. अगर आपने पासकी या पासवर्ड लागू किए हैं, तो एक साथ सभी ज़रूरी क्रेडेंशियल टाइप के लिए अनुरोध किया जा सकता है. इससे उपयोगकर्ता को यह याद रखने की ज़रूरत नहीं होगी कि उसने पहले साइन इन करने के लिए किस विकल्प का इस्तेमाल किया था.
अपने ऐप्लिकेशन के यूज़र इंटरफ़ेस (यूआई) में, 'Google से साइन इन करें' बटन जोड़ें. 'Google से साइन इन करें' बटन की मदद से, लोग अपने मौजूदा Google खातों का इस्तेमाल करके Android ऐप्लिकेशन में साइन अप या साइन इन कर सकते हैं. अगर उपयोगकर्ता बॉटम शीट यूज़र इंटरफ़ेस (यूआई) को खारिज करते हैं या उन्हें साइन अप और साइन इन करने के लिए, अपने Google खाते का इस्तेमाल करना है, तो वे 'Google से साइन इन करें' बटन पर क्लिक करेंगे. डेवलपर के लिए इसका मतलब है कि उपयोगकर्ताओं को आसानी से शामिल किया जा सकता है और साइन-अप के दौरान रुकावटें कम आती हैं.
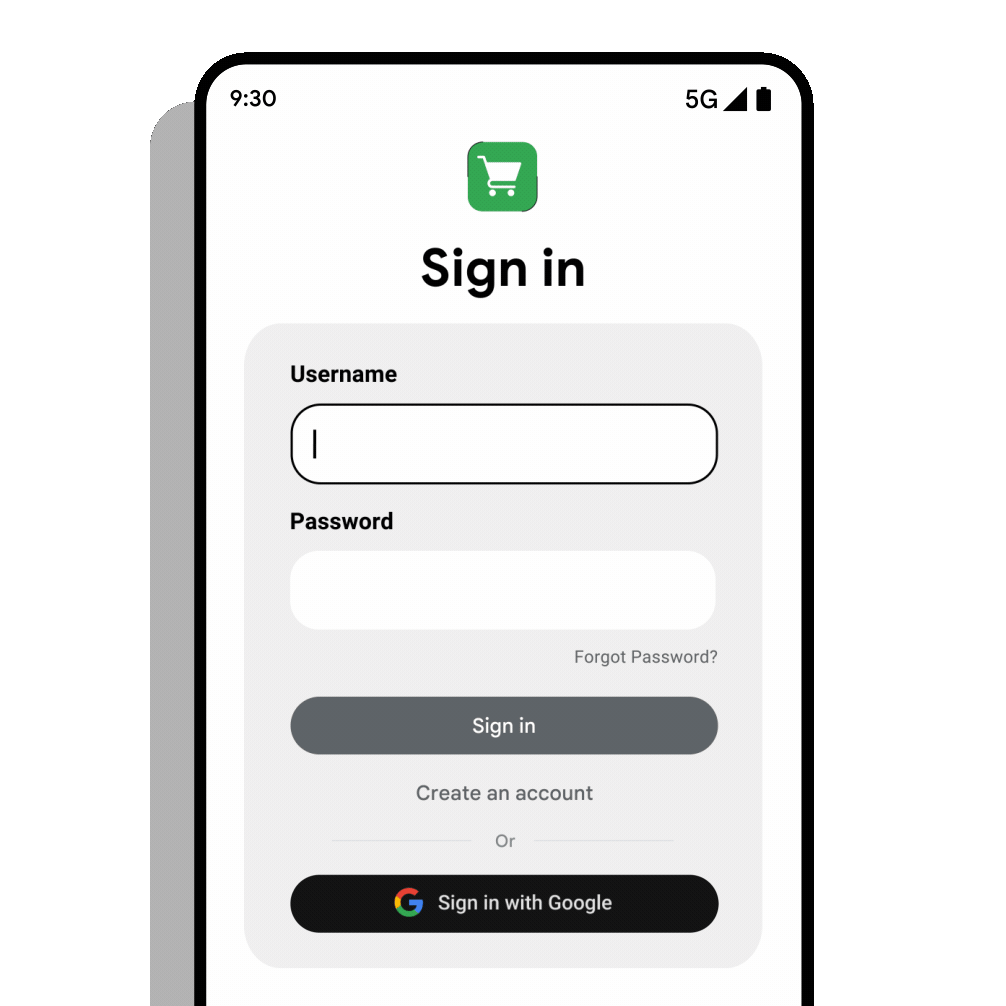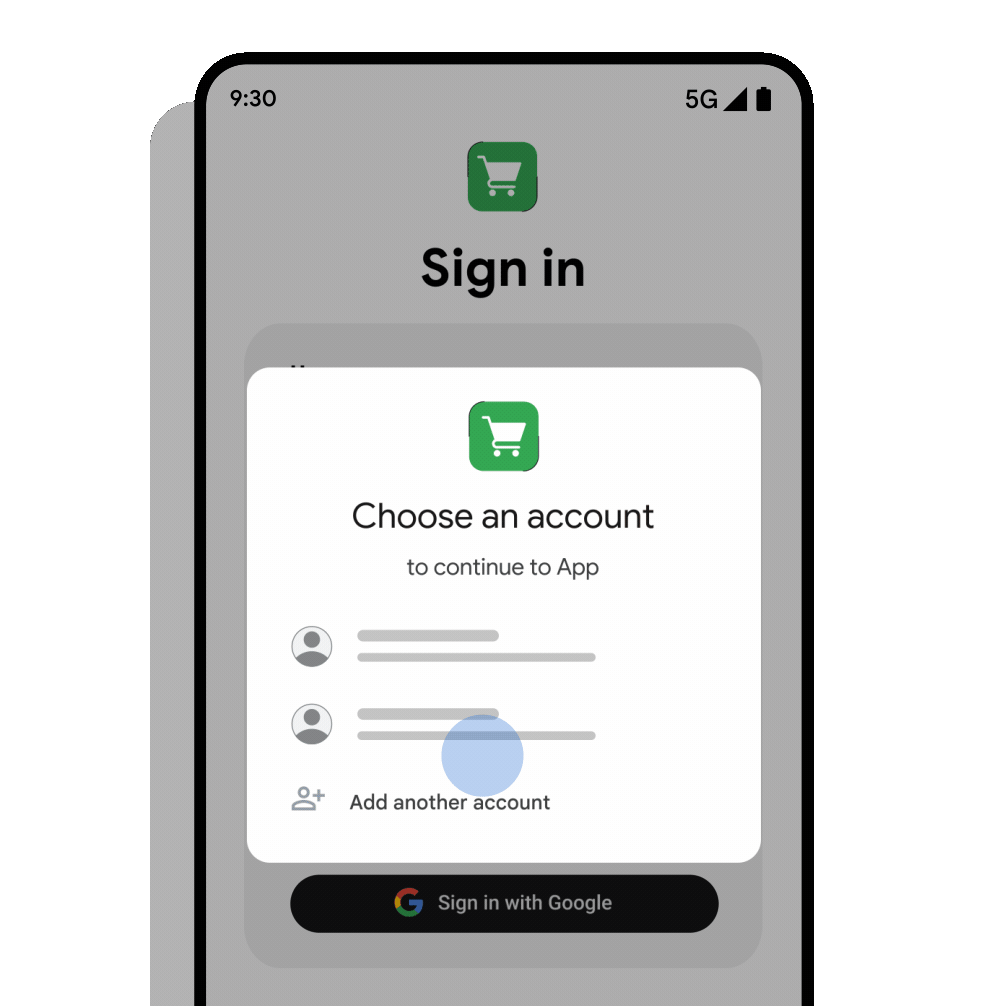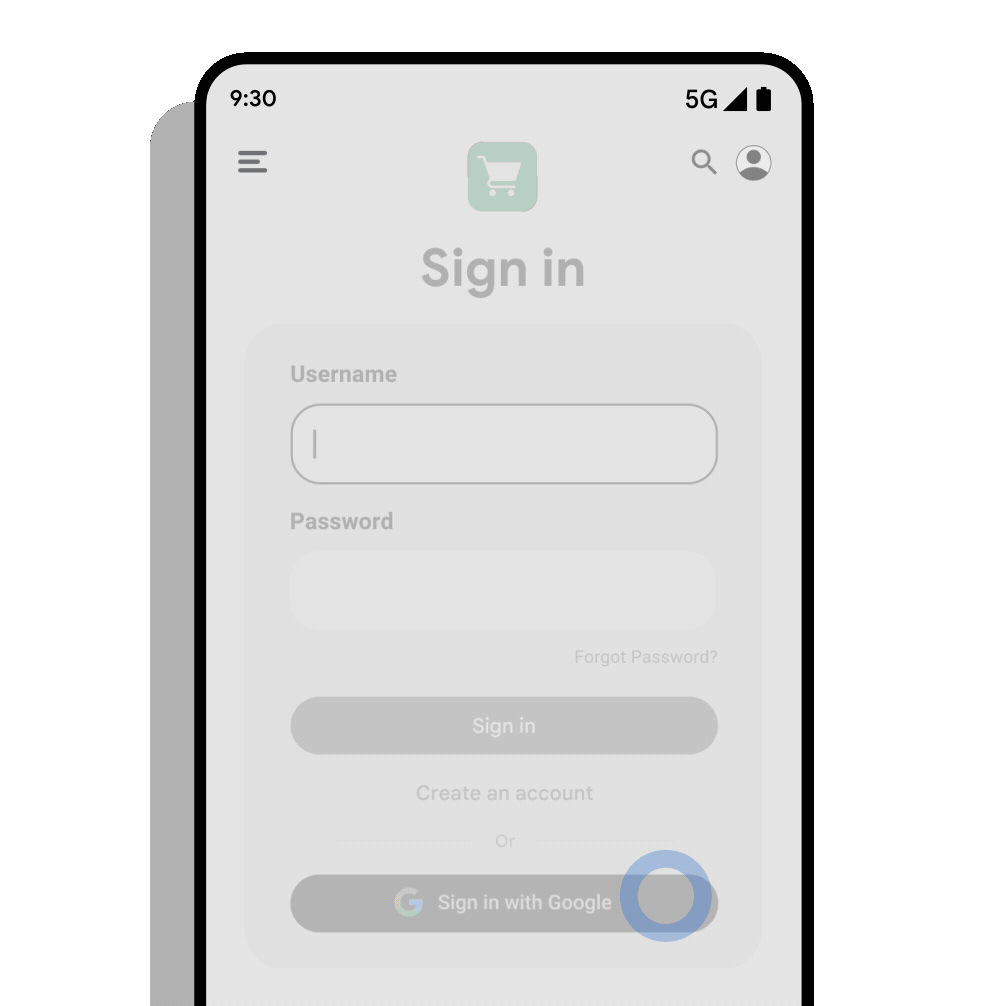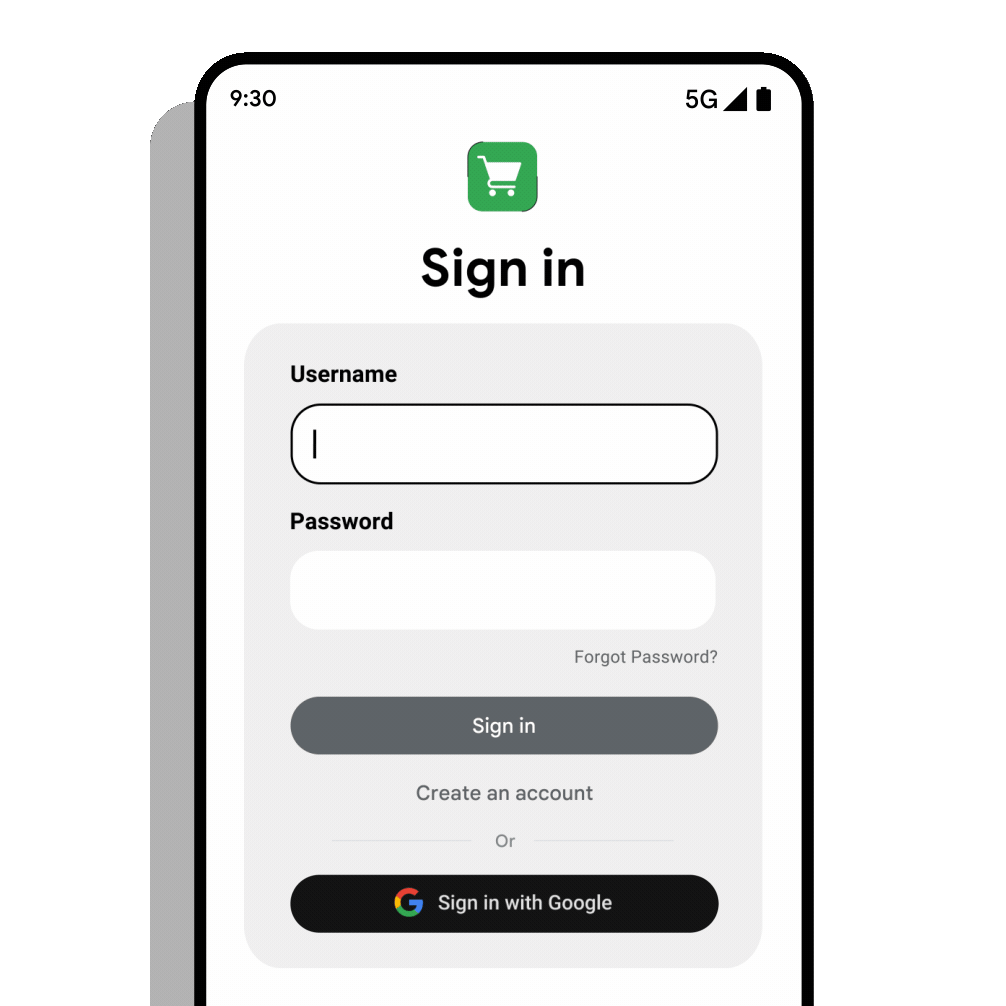
इस दस्तावेज़ में, Google ID हेल्पर लाइब्रेरी का इस्तेमाल करके, Credential Manager API के साथ 'Google से साइन इन करें' बटन और बॉटम शीट डायलॉग को इंटिग्रेट करने का तरीका बताया गया है.
अपना Google Cloud Console प्रोजेक्ट सेट अप करना
- Cloud Console में अपना प्रोजेक्ट खोलें. अगर आपके पास पहले से कोई प्रोजेक्ट नहीं है, तो एक प्रोजेक्ट बनाएं.
- Branding page पर जाकर, पक्का करें कि दी गई सारी जानकारी पूरी और सटीक हो.
- पक्का करें कि आपके ऐप्लिकेशन के लिए सही ऐप्लिकेशन का नाम, ऐप्लिकेशन का लोगो, और ऐप्लिकेशन का होम पेज असाइन किया गया हो. ये वैल्यू, उपयोगकर्ताओं को साइन अप करने के दौरान 'Google से साइन इन करें' सुविधा के लिए सहमति वाली स्क्रीन पर और तीसरे पक्ष के ऐप्लिकेशन और सेवाओं वाली स्क्रीन पर दिखेंगी.
- पक्का करें कि आपने अपने ऐप्लिकेशन की निजता नीति और सेवा की शर्तों के यूआरएल दिए हों.
- अगर आपके पास पहले से कोई Android क्लाइंट आईडी नहीं है, तो Clients page में जाकर, अपने ऐप्लिकेशन के लिए एक Android क्लाइंट आईडी बनाएं. आपको अपने ऐप्लिकेशन के पैकेज का नाम और SHA-1 हस्ताक्षर बताना होगा.
- Clients page पर जाएं.
- क्लाइंट खाता बनाएं पर क्लिक करें.
- Android ऐप्लिकेशन टाइप चुनें.
- OAuth क्लाइंट के लिए कोई नाम डालें. यह नाम आपके प्रोजेक्ट केClients page पर दिखता है, ताकि क्लाइंट की पहचान की जा सके.
- अपने Android ऐप्लिकेशन का पैकेज नाम डालें. यह वैल्यू, आपकी
AndroidManifest.xmlफ़ाइल में मौजूदpackageएट्रिब्यूट की<manifest>एलिमेंट में तय की जाती है. - ऐप्लिकेशन डिस्ट्रिब्यूशन के लिए, SHA-1 साइनिंग सर्टिफ़िकेट का फ़िंगरप्रिंट डालें.
- अगर आपका ऐप्लिकेशन Google Play की ऐप्लिकेशन साइनिंग सेवा का इस्तेमाल करता है, तो Play Console के ऐप्लिकेशन साइनिंग पेज से SHA-1 फ़िंगरप्रिंट कॉपी करें.
- अगर आपको अपने कीस्टोर और हस्ताक्षर करने वाली कुंजियों को मैनेज करना है, तो Java के साथ शामिल keytool यूटिलिटी का इस्तेमाल करें. इससे, सर्टिफ़िकेट की जानकारी को ऐसे फ़ॉर्मैट में प्रिंट किया जा सकता है जिसे आसानी से पढ़ा जा सके. keytool के आउटपुट के
Certificate fingerprintsसेक्शन में मौजूदSHA-1वैल्यू को कॉपी करें. ज़्यादा जानकारी के लिए, Android के लिए Google APIs के दस्तावेज़ में अपने क्लाइंट की पुष्टि करना लेख पढ़ें. - (ज़रूरी नहीं) अपने Android ऐप्लिकेशन के मालिकाना हक की पुष्टि करें.
- अगर आपने अब तक नया "वेब ऐप्लिकेशन" क्लाइंट आईडी नहीं बनाया है, तो Clients page में जाकर, नया क्लाइंट आईडी बनाएं. फ़िलहाल, "अनुमति वाले JavaScript ऑरिजिन" और "अनुमति वाले रीडायरेक्ट यूआरआई" फ़ील्ड को अनदेखा किया जा सकता है. इस क्लाइंट आईडी का इस्तेमाल, Google की पुष्टि करने वाली सेवाओं के साथ कम्यूनिकेट करते समय, आपके बैकएंड सर्वर की पहचान करने के लिए किया जाएगा.
- Clients page पर जाएं.
- क्लाइंट खाता बनाएं पर क्लिक करें.
- वेब ऐप्लिकेशन टाइप चुनें.
ऐप्लिकेशन के मालिकाना हक की पुष्टि करना
ऐप्लिकेशन के मालिकाना हक की पुष्टि करके, ऐप्लिकेशन के नाम पर धोखाधड़ी करने के जोखिम को कम किया जा सकता है.
पुष्टि की प्रक्रिया पूरी करने के लिए, अपने Google Play डेवलपर खाते का इस्तेमाल किया जा सकता है. हालांकि, इसके लिए ज़रूरी है कि आपके पास यह खाता हो और आपका ऐप्लिकेशन Google Play Console पर रजिस्टर हो. पुष्टि की प्रक्रिया पूरी करने के लिए, ये ज़रूरी शर्तें पूरी होनी चाहिए:
- आपके पास Google Play Console में रजिस्टर किया गया एक ऐसा ऐप्लिकेशन होना चाहिए जिसका पैकेज नाम और SHA-1 साइनिंग सर्टिफ़िकेट फ़िंगरप्रिंट, उस Android OAuth क्लाइंट के जैसा हो जिसकी पुष्टि की जा रही है.
- आपके पास Google Play Console में ऐप्लिकेशन के लिए, एडमिन की अनुमति होनी चाहिए. Google Play Console में ऐक्सेस मैनेज करने के बारे में ज़्यादा जानें.
Android क्लाइंट के ऐप्लिकेशन के मालिकाना हक की पुष्टि करें सेक्शन में, पुष्टि की प्रोसेस पूरी करने के लिए मालिकाना हक की पुष्टि करें बटन पर क्लिक करें.
पुष्टि हो जाने पर, आपको एक सूचना मिलेगी. इससे आपको पता चलेगा कि पुष्टि की प्रक्रिया पूरी हो गई है. ऐसा न करने पर, गड़बड़ी का मैसेज दिखेगा.
पुष्टि न हो पाने की समस्या को ठीक करने के लिए, यह तरीका आज़माएं:
- पक्का करें कि जिस ऐप्लिकेशन की पुष्टि की जा रही है वह Google Play Console में रजिस्टर किया गया हो.
- पक्का करें कि आपके पास Google Play Console में ऐप्लिकेशन के लिए, एडमिन की अनुमति हो.
डिपेंडेंसी का एलान करना
अपने ऐप्लिकेशन मॉड्यूल की बिल्ड स्क्रिप्ट में ये डिपेंडेंसी जोड़ें. पक्का करें कि आपने <latest version> को googleid लाइब्रेरी के नए वर्शन से बदल दिया हो:
Kotlin
dependencies { implementation("androidx.credentials:credentials:1.6.0-rc01") implementation("androidx.credentials:credentials-play-services-auth:1.6.0-rc01") implementation("com.google.android.libraries.identity.googleid:googleid:<latest version>") }
Groovy
dependencies { implementation "androidx.credentials:credentials:1.6.0-rc01" implementation "androidx.credentials:credentials-play-services-auth:1.6.0-rc01" implementation "com.google.android.libraries.identity.googleid:googleid:<latest version>" }
Google साइन-इन के अनुरोध को इंस्टैंशिएट करना
इसे लागू करने के लिए, Google साइन-इन के अनुरोध को इंस्टैंशिएट करें. किसी उपयोगकर्ता का Google आईडी टोकन वापस पाने के लिए, GetGoogleIdOption का इस्तेमाल करें.
val googleIdOption: GetGoogleIdOption = GetGoogleIdOption.Builder()
.setFilterByAuthorizedAccounts(true)
.setServerClientId(WEB_CLIENT_ID)
.setAutoSelectEnabled(true)
// nonce string to use when generating a Google ID token
.setNonce(nonce)
.build()
सबसे पहले, यह देखें कि उपयोगकर्ता के पास ऐसे खाते हैं या नहीं जिनका इस्तेमाल पहले आपके ऐप्लिकेशन में साइन इन करने के लिए किया गया था. इसके लिए, एपीआई को setFilterByAuthorizedAccounts पैरामीटर के साथ कॉल करें और true पर सेट करें. उपयोगकर्ता, साइन इन करने के लिए उपलब्ध खातों में से कोई एक खाता चुन सकते हैं.
अगर कोई भी मान्य Google खाता उपलब्ध नहीं है, तो उपयोगकर्ता को उपलब्ध किसी भी खाते से साइन अप करने के लिए कहा जाना चाहिए. इसके लिए, एपीआई को फिर से कॉल करके उपयोगकर्ता को सूचना दें और setFilterByAuthorizedAccounts को false पर सेट करें.
साइन अप करने के बारे में ज़्यादा जानें.
दोबारा आने वाले उपयोगकर्ताओं के लिए, अपने-आप साइन-इन होने की सुविधा चालू करें (सुझाया गया)
डेवलपर को उन उपयोगकर्ताओं के लिए अपने-आप साइन-इन होने की सुविधा चालू करनी चाहिए जो एक ही खाते से रजिस्टर करते हैं. इससे अलग-अलग डिवाइसों पर एक जैसा अनुभव मिलता है. खास तौर पर, डिवाइस माइग्रेट करने के दौरान, उपयोगकर्ता अपने खाते को तुरंत ऐक्सेस कर सकते हैं. इसके लिए, उन्हें फिर से क्रेडेंशियल डालने की ज़रूरत नहीं होती. अगर आपके उपयोगकर्ताओं ने पहले से साइन इन किया हुआ है, तो इससे उन्हें बिना किसी रुकावट के ऐक्सेस मिल जाता है.
अपने-आप साइन-इन होने की सुविधा चालू करने के लिए, setAutoSelectEnabled(true) का इस्तेमाल करें. अपने-आप साइन इन होने की सुविधा सिर्फ़ तब काम करती है, जब ये शर्तें पूरी की गई हों:
- अनुरोध से मेल खाने वाला एक ही क्रेडेंशियल मौजूद है. यह क्रेडेंशियल, Google खाता या पासवर्ड हो सकता है. साथ ही, यह क्रेडेंशियल, Android डिवाइस पर मौजूद डिफ़ॉल्ट खाते से मेल खाता है.
- उपयोगकर्ता ने साफ़ तौर पर साइन आउट नहीं किया है.
- उपयोगकर्ता ने Google खाते की सेटिंग में, अपने-आप साइन इन होने की सुविधा बंद न की हो.
val googleIdOption: GetGoogleIdOption = GetGoogleIdOption.Builder()
.setFilterByAuthorizedAccounts(true)
.setServerClientId(WEB_CLIENT_ID)
.setAutoSelectEnabled(true)
// nonce string to use when generating a Google ID token
.setNonce(nonce)
.build()
अपने-आप साइन इन होने की सुविधा लागू करते समय, साइन-आउट करने की सुविधा को सही तरीके से मैनेज करना न भूलें. इससे उपयोगकर्ता, आपके ऐप्लिकेशन से साइन आउट करने के बाद, हमेशा सही खाता चुन पाएंगे.
सुरक्षा को बेहतर बनाने के लिए, एक नॉनस सेट करना
साइन इन करने की सुरक्षा को बेहतर बनाने और रीप्ले हमलों से बचने के लिए, हर अनुरोध में नॉन्स शामिल करने के लिए setNonce जोड़ें. नॉन्स जनरेट करने के बारे में
ज़्यादा जानें.
val googleIdOption: GetGoogleIdOption = GetGoogleIdOption.Builder()
.setFilterByAuthorizedAccounts(true)
.setServerClientId(WEB_CLIENT_ID)
.setAutoSelectEnabled(true)
// nonce string to use when generating a Google ID token
.setNonce(nonce)
.build()
'Google से साइन इन करें' सुविधा का फ़्लो बनाना
'Google से साइन इन करें' फ़्लो सेट अप करने का तरीका यहां दिया गया है:
GetCredentialRequestको इंस्टैंशिएट करें. इसके बाद, क्रेडेंशियल पाने के लिए, पहले से बनाए गएgoogleIdOptionकोaddCredentialOption()का इस्तेमाल करके जोड़ें.- उपयोगकर्ता के उपलब्ध क्रेडेंशियल पाने के लिए, इस अनुरोध को
getCredential()(Kotlin) याgetCredentialAsync()(Java) कॉल पर भेजें. - एपीआई के काम करने के बाद,
CustomCredentialनिकालें. इसमेंGoogleIdTokenCredentialडेटा का नतीजा होता है. CustomCredentialका टाइप,GoogleIdTokenCredential.TYPE_GOOGLE_ID_TOKEN_CREDENTIALकी वैल्यू के बराबर होना चाहिए.GoogleIdTokenCredential.createFromतरीके का इस्तेमाल करके, ऑब्जेक्ट कोGoogleIdTokenCredentialमें बदलें.अगर कन्वर्ज़न पूरा हो जाता है, तो
GoogleIdTokenCredentialआईडी निकालें, उसकी पुष्टि करें, और अपने सर्वर पर क्रेडेंशियल की पुष्टि करें.अगर
GoogleIdTokenParsingExceptionके साथ कन्वर्ज़न नहीं होता है, तो आपको Sign in with Google लाइब्रेरी का वर्शन अपडेट करना पड़ सकता है.पहचान न किए गए कस्टम क्रेडेंशियल टाइप का पता लगाएं.
val request: GetCredentialRequest = GetCredentialRequest.Builder()
.addCredentialOption(googleIdOption)
.build()
coroutineScope {
try {
val result = credentialManager.getCredential(
request = request,
context = activityContext,
)
handleSignIn(result)
} catch (e: GetCredentialException) {
// Handle failure
}
}
fun handleSignIn(result: GetCredentialResponse) {
// Handle the successfully returned credential.
val credential = result.credential
val responseJson: String
when (credential) {
// Passkey credential
is PublicKeyCredential -> {
// Share responseJson such as a GetCredentialResponse to your server to validate and
// authenticate
responseJson = credential.authenticationResponseJson
}
// Password credential
is PasswordCredential -> {
// Send ID and password to your server to validate and authenticate.
val username = credential.id
val password = credential.password
}
// GoogleIdToken credential
is CustomCredential -> {
if (credential.type == GoogleIdTokenCredential.TYPE_GOOGLE_ID_TOKEN_CREDENTIAL) {
try {
// Use googleIdTokenCredential and extract the ID to validate and
// authenticate on your server.
val googleIdTokenCredential = GoogleIdTokenCredential
.createFrom(credential.data)
// You can use the members of googleIdTokenCredential directly for UX
// purposes, but don't use them to store or control access to user
// data. For that you first need to validate the token:
// pass googleIdTokenCredential.getIdToken() to the backend server.
// see [validation instructions](https://developers.google.com/identity/gsi/web/guides/verify-google-id-token)
} catch (e: GoogleIdTokenParsingException) {
Log.e(TAG, "Received an invalid google id token response", e)
}
} else {
// Catch any unrecognized custom credential type here.
Log.e(TAG, "Unexpected type of credential")
}
}
else -> {
// Catch any unrecognized credential type here.
Log.e(TAG, "Unexpected type of credential")
}
}
}
'Google से साइन इन करें' बटन का फ़्लो ट्रिगर करना
'Google से साइन इन करें' बटन के फ़्लो को ट्रिगर करने के लिए, GetGoogleIdOption के बजाय GetSignInWithGoogleOption का इस्तेमाल करें:
val signInWithGoogleOption: GetSignInWithGoogleOption = GetSignInWithGoogleOption.Builder(
serverClientId = WEB_CLIENT_ID
).setNonce(nonce)
.build()
GoogleIdTokenCredential को मैनेज करने के लिए, यहां दिए गए कोड का उदाहरण देखें.
fun handleSignInWithGoogleOption(result: GetCredentialResponse) {
// Handle the successfully returned credential.
val credential = result.credential
when (credential) {
is CustomCredential -> {
if (credential.type == GoogleIdTokenCredential.TYPE_GOOGLE_ID_TOKEN_CREDENTIAL) {
try {
// Use googleIdTokenCredential and extract id to validate and
// authenticate on your server.
val googleIdTokenCredential = GoogleIdTokenCredential
.createFrom(credential.data)
} catch (e: GoogleIdTokenParsingException) {
Log.e(TAG, "Received an invalid google id token response", e)
}
} else {
// Catch any unrecognized credential type here.
Log.e(TAG, "Unexpected type of credential")
}
}
else -> {
// Catch any unrecognized credential type here.
Log.e(TAG, "Unexpected type of credential")
}
}
}
Google से साइन इन करने का अनुरोध शुरू करने के बाद, पुष्टि करने की प्रोसेस शुरू करें. यह प्रोसेस, Sign in with Google सेक्शन में बताई गई प्रोसेस की तरह ही होनी चाहिए.
नए उपयोगकर्ताओं के लिए साइन-अप करने की सुविधा चालू करें (सुझाया गया)
'Google से साइन इन करें' सुविधा, उपयोगकर्ताओं के लिए आपके ऐप्लिकेशन या सेवा पर नया खाता बनाने का सबसे आसान तरीका है. इसके लिए, उन्हें सिर्फ़ कुछ बार टैप करना होता है.
अगर सेव किए गए क्रेडेंशियल नहीं मिलते हैं (getGoogleIdOption से कोई Google खाता नहीं मिलता है), तो अपने उपयोगकर्ता को साइन अप करने के लिए कहें. सबसे पहले, setFilterByAuthorizedAccounts(true) पर जाकर देखें कि क्या पहले इस्तेमाल किए गए कोई खाते मौजूद हैं. अगर कोई भी खाता नहीं मिलता है, तो उपयोगकर्ता को अपने Google खाते से साइन अप करने के लिए कहें. इसके लिए, setFilterByAuthorizedAccounts(false) का इस्तेमाल करें
उदाहरण:
val googleIdOption: GetGoogleIdOption = GetGoogleIdOption.Builder()
.setFilterByAuthorizedAccounts(false)
.setServerClientId(WEB_CLIENT_ID)
.build()
Google से साइन अप करने का अनुरोध शुरू करने के बाद, पुष्टि करने की प्रोसेस शुरू करें. अगर उपयोगकर्ता साइन अप करने के लिए, 'Google से साइन इन करें' सुविधा का इस्तेमाल नहीं करना चाहते हैं, तो अपने ऐप्लिकेशन को अपने-आप भरने की सुविधा के लिए ऑप्टिमाइज़ करें. जब आपका उपयोगकर्ता खाता बना लेता है, तो खाता बनाने की प्रोसेस के आखिरी चरण के तौर पर, उसे पासकी में रजिस्टर करें.
साइन आउट करने की सुविधा
जब कोई उपयोगकर्ता आपके ऐप्लिकेशन से साइन आउट करता है, तो एपीआई clearCredentialState()
मेथड को कॉल करें. इससे क्रेडेंशियल की सेवा देने वाली सभी कंपनियों से, मौजूदा उपयोगकर्ता के क्रेडेंशियल की स्थिति मिट जाएगी.
इससे क्रेडेंशियल देने वाली सभी कंपनियों को सूचना मिलेगी कि दिए गए ऐप्लिकेशन के लिए सेव किए गए क्रेडेंशियल सेशन को मिटा दिया जाए.
क्रेडेंशियल देने वाली कंपनी ने सक्रिय क्रेडेंशियल सेशन को सेव किया हो सकता है. साथ ही, इसका इस्तेमाल आने वाले समय में क्रेडेंशियल पाने के लिए किए जाने वाले कॉल के लिए, साइन-इन के विकल्पों को सीमित करने के लिए किया जा सकता है. उदाहरण के लिए, यह उपलब्ध किसी भी अन्य क्रेडेंशियल के मुकाबले, चालू क्रेडेंशियल को प्राथमिकता दे सकता है. जब आपका उपयोगकर्ता, आपके ऐप्लिकेशन से साफ़ तौर पर साइन आउट करता है और अगली बार साइन-इन करने के सभी विकल्प पाने के लिए, आपको इस एपीआई को कॉल करना चाहिए. इससे सेवा देने वाली कंपनी, सेव किए गए क्रेडेंशियल सेशन को मिटा सकेगी.
