Program Peningkatan Keamanan Aplikasi adalah layanan yang disediakan kepada developer aplikasi Google Play untuk meningkatkan keamanan aplikasi mereka. Program ini memberikan tips dan rekomendasi dalam membuat aplikasi yang lebih aman dan mengidentifikasi potensi peningkatan keamanan saat aplikasi Anda diupload ke Google Play. Hingga saat ini, program ini telah mempermudah developer dalam memperbaiki lebih dari 1.000.000 aplikasi di Google Play.
Cara kerja
Sebelum aplikasi diterima di Google Play, kami memindainya demi keselamatan dan keamanan, termasuk potensi masalah keamanan. Kami juga terus memindai ulang lebih dari satu juta aplikasi di Google Play untuk mengidentifikasi ancaman tambahan.
Jika aplikasi Anda ditandai karena potensi masalah keamanan, kami akan segera memberi tahu Anda untuk membantu mengatasi masalah tersebut dengan cepat dan menjaga keamanan pengguna. Kami akan mengirimkan notifikasi kepada Anda menggunakan email dan Konsol Google Play, yang berisi link ke halaman dukungan dengan detail tentang cara memperbaiki aplikasi.
Umumnya, notifikasi ini akan menyertakan linimasa untuk mengirimkan perbaikan kepada pengguna secepat mungkin. Untuk beberapa jenis masalah, Anda mungkin harus melakukan peningkatan keamanan di aplikasi sebelum dapat memublikasikan update lain bagi aplikasi tersebut.
Anda dapat mengonfirmasi bahwa Anda sudah sepenuhnya mengatasi masalah tersebut dengan mengupload versi baru aplikasi ke Konsol Google Play. Pastikan untuk meningkatkan nomor versi aplikasi yang telah diperbaiki. Setelah beberapa jam, periksa pemberitahuan keamanan di Konsol Play; jika sudah tidak ada lagi, artinya masalah sudah teratasi.
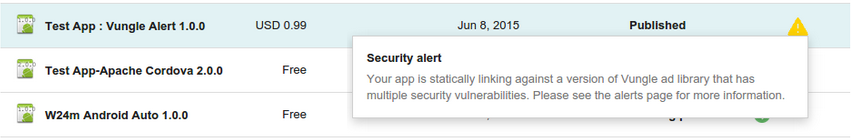
Contoh pemberitahuan peningkatan keamanan untuk aplikasi di Konsol Play.
Libatkan diri
Keberhasilan program ini bergantung pada kemitraan kami dengan Anda—selaku developer aplikasi di Google Play—dan komunitas keamanan. Kita semua bertanggung jawab untuk menyediakan aplikasi yang aman dan terlindungi bagi pengguna. Untuk mengirim masukan atau pertanyaan, hubungi kami melalui Pusat Bantuan Developer Google Play. Untuk melaporkan potensi masalah keamanan di aplikasi, hubungi kami di security+asi@android.com.
Kampanye dan perbaikan
Berikut adalah masalah keamanan terbaru yang dilaporkan kepada developer di Google Play. Detail informasi kerentanan dan perbaikan tersedia di setiap link halaman dukungan kampanye.
Tabel 1: Kampanye peringatan dengan batas waktu perbaikan terkait.
| Kampanye | Dimulai | Halaman Dukungan |
|---|---|---|
| Kunci Server Firebase Cloud Messaging yang terekspos | 10/12/2021 | Halaman Dukungan |
| Pengalihan Intent | 16/5/2019 | Halaman dukungan |
| Injeksi Antarmuka JavaScript | 4/12/2018 | Halaman dukungan |
| Pembajakan Skema | 15/11/2018 | Halaman dukungan |
| Pembuatan Skrip Lintas Aplikasi | 30/10/2018 | Halaman dukungan |
| Pembuatan Skrip Lintas Situs berbasis file | 5/6/2018 | Halaman dukungan |
| Injeksi SQL | 4/6/2018 | Halaman dukungan |
| Path Traversal | 22/9/2017 | Halaman dukungan |
| Verifikasi Hostname Tidak Aman | 29/11/2016 | Halaman dukungan |
| Injeksi Fragmen | 29/11/2016 | Halaman dukungan |
| SDK Iklan Supersonic | 28/9/2016 | Halaman dukungan |
| Libpng | 16/6/2016 | Halaman dukungan |
| Libjpeg-turbo | 16/6/2016 | Halaman dukungan |
| SDK Iklan Vpon | 16/6/2016 | Halaman dukungan |
| SDK Iklan Airpush | 31/3/2016 | Halaman dukungan |
| SDK Iklan MoPub | 31/3/2016 | Halaman dukungan |
| OpenSSL (“logjam” dan CVE-2015-3194, CVE-2014-0224) | 31/3/2016 | Halaman dukungan |
| TrustManager | 17/2/2016 | Halaman dukungan |
| AdMarvel | 8/2/2016 | Halaman dukungan |
| Libupup (CVE-2015-8540) | 8/2/2016 | Halaman dukungan |
| Apache Cordova (CVE-2015-5256, CVE-2015-1835) | 14/12/2015 | Halaman dukungan |
| SDK Iklan Vitamio | 14/12/2015 | Halaman dukungan |
| GnuTLS | 13/10/2015 | Halaman dukungan |
| Webview SSLErrorHandler | 17/7/2015 | Halaman dukungan |
| SDK Iklan Vungle | 29/6/2015 | Halaman dukungan |
| Apache Cordova (CVE-2014-3500, CVE-2014-3501, CVE-2014-3502) | 29/6/2015 | Halaman dukungan |
Tabel 2: Kampanye khusus peringatan (tidak ada batas waktu perbaikan).
| Kampanye | Dimulai | Halaman Dukungan |
|---|---|---|
| PendingIntent Implisit | 22/2/2022 | Halaman dukungan |
| Intent Internal Implisit | 6/22/2021 | Halaman dukungan |
| Mode Enkripsi Tidak Aman | 10/13/2020 | Halaman dukungan |
| Enkripsi Tidak Aman | 9/17/2019 | Halaman dukungan |
| Path Traversal Zipfile | 21/5/2019 | Halaman dukungan |
| Token OAuth Foursquare Tersemat | 28/9/2016 | Halaman dukungan |
| Token OAuth Facebook Tersemat | 28/9/2016 | Halaman dukungan |
| Intersepsi Layanan Penagihan Google Play | 28/7/2016 | Halaman dukungan |
| OAuth Token Refresh Google Tersemat | 28/7/2016 | Halaman dukungan |
| Kebocoran Kredensial URL Developer | 16/6/2016 | Halaman dukungan |
| File Keystore Tersemat | 2/10/2014 | |
| Kredensial tersemat Amazon Web Services | 12/6/2014 |
