OWASP カテゴリ: MASVS-PLATFORM: プラットフォームのインタラクション
概要
タップジャッキングは、クリックジャッキング ウェブ脆弱性の Android アプリ版です。具体的には、悪意のあるアプリが、オーバーレイなどの手段で UI を不明瞭にし、ユーザーをだましてセキュリティ関連のコントロール(確認ボタンなど)をクリックするよう仕向けます。ここでは、この攻撃の 2 つの亜種(完全オクルージョンと部分オクルージョン)について説明します。完全オクルージョンでは、タッチエリアがオーバーレイされますが、部分オクルージョンでタッチエリアが不明瞭にされることはありません。
影響
タップジャッキング攻撃は、ユーザーをだまして特定のアクションを実行させるために使用されます。この影響は、標的にされるアクションによって異なります。
リスク: 完全オクルージョン
完全オクルージョンでは、タッチエリアがオーバーレイされ、タッチイベントがハイジャックされます。
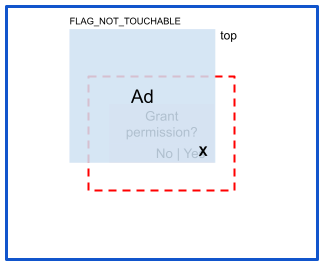
リスクの軽減
完全オクルージョンを防ぐには、コードで View.setFilterTouchesWhenObscured(true) を設定します。これにより、オーバーレイから渡されたタッチがブロックされます。宣言型の方法を使う場合は、保護する View オブジェクトのレイアウト ファイルに android:filterTouchesWhenObscured="true" を追加します。
リスク: 部分オクルージョン
部分オクルージョン攻撃では、タッチエリアが不明瞭になることはありません。
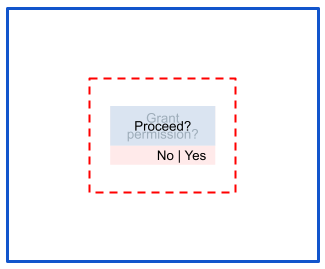
リスクの軽減
部分オクルージョンは、FLAG_WINDOW_IS_PARTIALLY_OBSCURED フラグがあるタッチイベントを手動で無視することで軽減されます。このシナリオに対するデフォルトの保護機能はありません。
考えられる注意点: この軽減策は、無害なアプリを妨げる可能性があります。一部のケースでは、無害なアプリにより部分オクルージョンが発生するとユーザー エクスペリエンスに悪影響があるため、この修正をリリースできません。
特定のリスク
このセクションでは、標準的でない軽減戦略が必要、または特定の SDK レベルで軽減されたリスクをまとめています。また、完全を期すためにその他のリスクも挙げています。
リスク: android.Manifest.permission.SYSTEM_ALERT_WINDOW
SYSTEM_ALERT_WINDOW 権限により、すべてのアプリの上部に表示されるウィンドウの作成が許可されます。
リスクの軽減
新しいバージョンの Android では、次のようないくつかの軽減策が導入されています。
- Android 6(API レベル 23)以降では、ユーザーが、オーバーレイ ウィンドウを作成する権限をアプリに対して明示的に付与する必要があります。
- Android 12(API レベル 31)以降では、アプリが
trueをWindow.setHideOverlayWindows()に渡すことができます。
リスク: カスタム トースト
攻撃者は Toast.setView() を使用してトースト メッセージの外観をカスタマイズできます。Android 10(API レベル 29)以前では、悪意のあるアプリがこのようなトーストをバックグラウンドから起動できました。
リスクの軽減
Android 11(API レベル 30)以降をターゲットとするアプリの場合、バックグラウンドのカスタム トーストがブロックされます。ただし、攻撃者がフォアグラウンドにいるときに複数のトーストをキューに入れ、アプリがバックグラウンドに移動した後も起動され続ける「トースト バースト」を使用する状況下では、この軽減策は回避されることがあります。
バックグラウンド トースト攻撃とトースト バースト攻撃は、Android 12(API レベル 31)以降で完全に対策されています。
リスク: アクティビティ サンドイッチ
悪意のあるアプリがユーザーを信用させて自身を開かせることに成功した場合、さらに侵害済みのアプリからアクティビティを起動した後、それに独自のアクティビティを重ねることで、「アクティビティ サンドイッチ」を形成して部分オクルージョン攻撃を行うことができます。
リスクの軽減
部分オクルージョンの一般的な軽減策をご覧ください。多層防御を行うため、エクスポートする必要のないアクティビティは、攻撃者がサンドイッチするのを防ぐためにエクスポートしないようにしてください。
参考資料
あなたへのおすすめ
- 注: JavaScript がオフになっている場合はリンクテキストが表示されます
- android:exported
- # キー管理 {:#key-management}
- APK から埋め込み DEX コードを直接実行する
